Financial data represent an Eldorado that’s much too accessible to hackers
By Risk Performance and Technology group
Original, as it appears on Finance et Investissement – https://www.finance-investissement.com/
“We’re not a bank!” This is the one statement that I have been hearing the most lately. Ultimately, it is a statement that seems to suggest that the banks supposedly need a much higher level of security than do other businesses in the financial and insurance industries, or even other industries.
In fact, as I have already explained in some of my articles, we are all targets who are trying our best not to become victims. Our data is a precious commodity that can be used against us or converted into money; it is worth something, regardless of who we are. Our financial, accounting, corporate, legal or property information, and that of your clients, is the subject of this article.
Remember: Pizza Hut revealed that its website and app had been hacked on October 1, with the personal information of an undisclosed number of clients at risk.
The hacking may have compromised billing information, including delivery addresses, email addresses and card payment information containing account numbers, expiry dates and CVV numbers.
Recently, Deloitte, one of the biggest accounting firms in the world, was also hacked. The hackers may have obtained details on the organization’s top clients, including usernames, passwords, personal data, and even confidential emails detailing private plans and documents.
Earlier this year, Equifax, the global banking information solutions company, announced a major cybersecurity incident that affected 143 million consumers in the United States. The breach—initially discovered on July 29—may have revealed the names, social security numbers, birth dates and addresses of nearly half of all Americans.
On July 13, 2017, Bupa’s data was compromised, which affected 500,000 of its clients holding an international health insurance plan. The London-based private healthcare group stated that a Bupa employee had inappropriately copied and deleted information, such as names, birth dates, and some contact information, but that no medical information had been compromised.
Loan company Wonga was the victim of a major data breach, possibly affecting up to 245,000 of its clients, that included client bank account numbers and risk scores.
In 2016, Benny Higgins, the general manager of Tesco Bank, stated in a press release published on the company’s website that 40,000 accounts had been compromised and that money had been stolen from half of them.
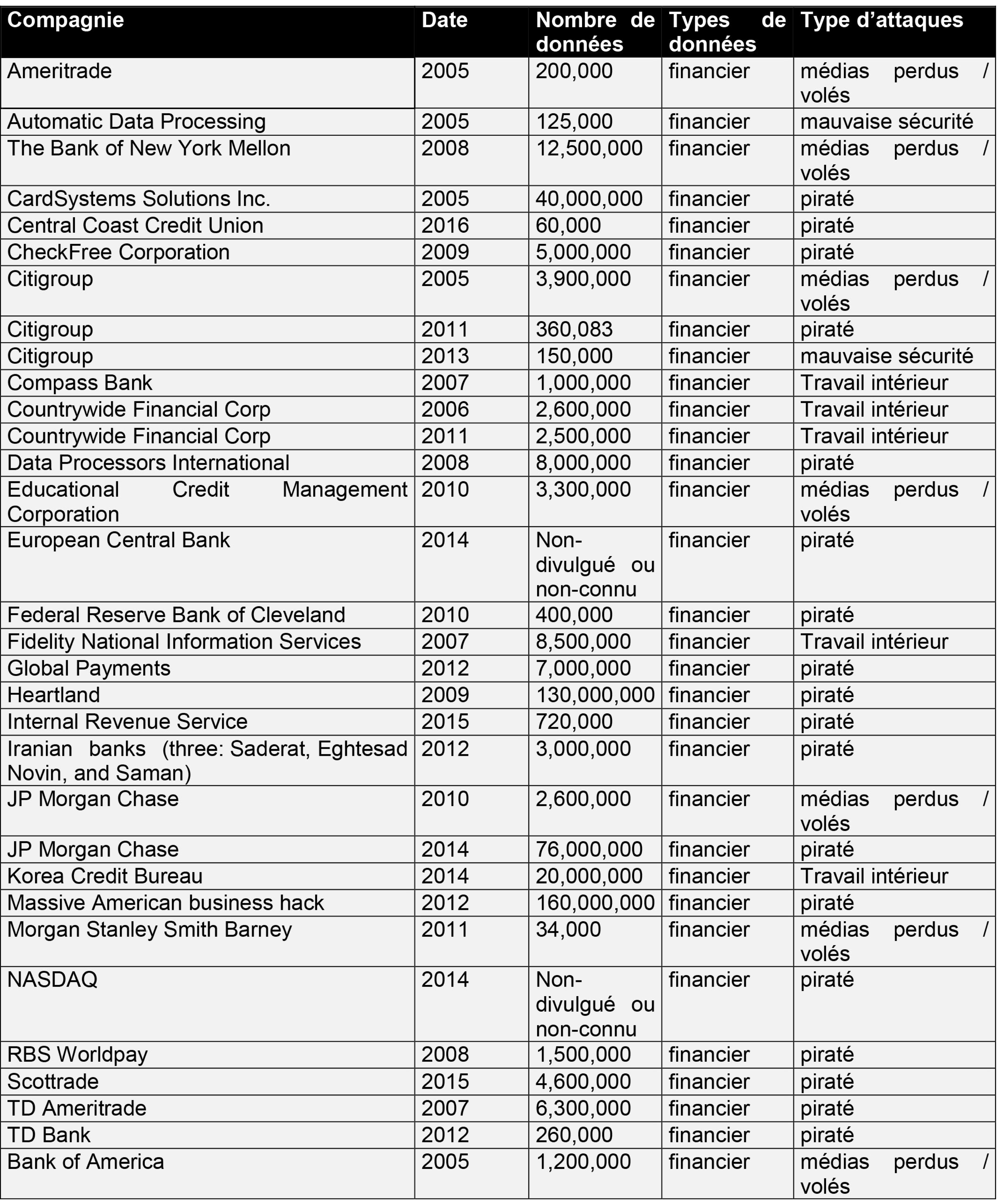
Below is a table maintained on Wikipedia showing the other most significant data breaches in the financial world:
The big issue here is that this data is advertised and sold on the Dark Web.
The data allows defrauders to improve their ability to commit online fraud, defraud the president, a bank technician, steal identities, extort money, and fraudulently lock clients out of their own bank account. All this often leads to the extortion of an enormous amount of money to insure against loss, fraud or theft.
Let’s take one more example—the data leak that occurred at Mossack-Fonseca and which led to the Panama Papers affair. How much data was leaked? A lot. The leak was one of the biggest ever published. In all, 11.5 million documents containing 2.6 terabytes of information were extracted from Mossack-Fonseca’s database. This volume of information was transferred little by little over several months to avoid raising any suspicions. Would you have been able to stop the hemorrhaging caused by this kind of cyberattack? Is your organization prepared to detect an internal cybercrime?
Here’s how to prevent this from happening:
- Have your personal and business presence on the Dark Web tested and verified professionally.
- Change your passwords regularly and do not use the same one for everything.
- Select a good, dynamic password and two-factor authentication.
- Question any unsolicited communication and be vigilant, because you know the wolf is on the hunt for you too.
More simply:
- Get in the habit of reading information about privacy: What personal information is being gathered? Does it make sense to you, given the service being offered? Will the information be communicated to a third party?
- Check if the supplier is committed to complying with security or privacy standards.
- Switch off devices connected to the Internet when you don’t need them. This advice applies to all “smart” devices.
- Turn off the wireless network when you’re not using it.
