The COVID-19 Pandemic: An Opportunity to Address IT Compliance Needs
Needless to say, the COVID-19 pandemic has brought with it a significant set of changes and challenges.
Now more than ever, many organizations are faced with unprecedented hurdles such as maintaining day-to-day operations while adapting to the new normal and ensuring everyone is safe and productive all at once. Control environments as well as the quality level of service a customer expects are not immune to this disruption and need for adjustment. We are witnessing exponential growth in the demand for different IT services as well as an accelerated emphasis on the digitization of processes in organizations of all sizes. More and more, we’re also seeing organizations outsource some, or in some instances, all, their key processes.
This can be where the uncertainty sets in.
With increased risks and obstacles, a business’ IT compliance needs to be sound and secure – period. Not only does this help protect you, your organization, your clients and data, but it can help make operations more efficient and uncover cost savings to help your bottom line.
Good governance and proper risk management require an organization to examine (among other things) the extent to which the third parties with whom the organization conducts business (i.e., service providers) have an impact on said organization’s security and compliance.
Whether you are evaluating a provider of infrastructure (Infrastructure-as-a-Service, or “IaaS”), platforms (Platform-as-a-Service, aka “PaaS”), software solutions (Software-as-a-Service, you guessed it, “SaaS”) or a data center offering colocation, there are multiple compliance requests you can make to ensure they are operating safely and effectively, as well as certificates which can help demonstrate that their cyber security program is well managed. In some cases, you may even want to consider requesting an independent assessment of compliance with standards such as CSAE 3416 and SSAE 18 before considering doing or continuing business with that provider.
System and Organization Controls (SOC) reports help service providers meet these compliance demands. They are issued by an independent auditor such as Richter and provide businesses (i.e., customers of the provider) with assurance about the service delivery processes and compliance with pre-determined controls.
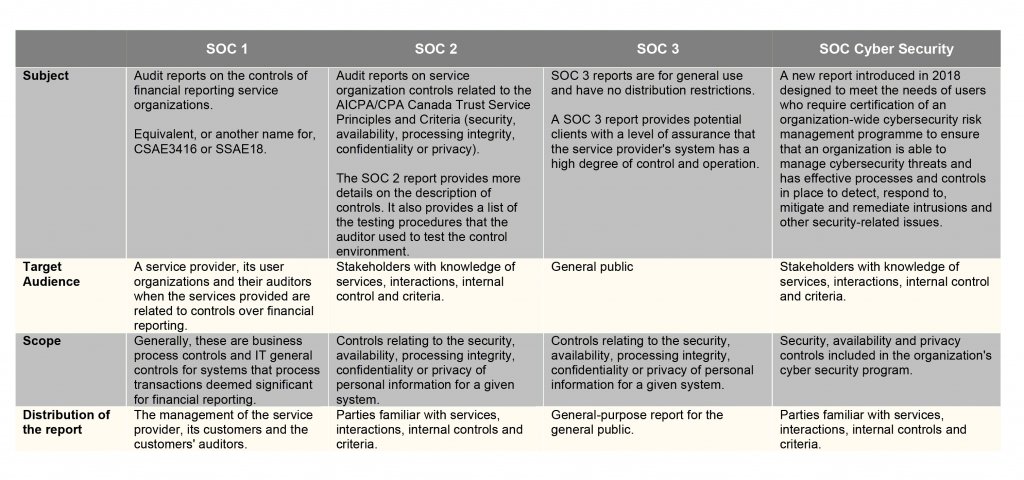
SOC 1, SOC 2, SOC 3, SOC Cyber Security … What is the right report?
It all depends on your objectives. The following table highlights the main differences between the different types of reports:
How can Richter help you?
- Readiness Assessments – Richter will assess your organization’s readiness and help define the scope by assisting you and/or your senior management team in developing a system description to be included in the scope of the report. We can also assist by documenting existing control procedures, identifying potential control deficiencies and making realistic recommendations for improvement.
- SOC audit reports – Depending on compliance requirements and the scope of the audit, a SOC report will provide an independent assessment of an organization’s internal controls. Richter will help determine the type of audit report a service organization needs and will conduct the related audit in accordance with CPA Canada or AICPA standards. We offer certification services for all types of SOC reports (1, 2, 3 and Cyber Security).
