Cybersecurity
It’s every company’s worst nightmare: a cyber-attack paralyzes your systems, puts your confidential information and finances at risk, and threatens to compromise your employees’ and clients’ personal data. Such attacks can cripple an organization or, even worse, put it out of business for good.
Are you prepared?
When it comes to cybersecurity, a firewall and an antivirus solution are barely the tip of the security iceberg by today’s standards. Attacks on companies of all sizes are increasing in frequency and scope. Companies of all sizes and in any industry can become the target of a cyber-attack. It’s no longer a question of whether your company will experience a cyber-attack but when.
Ignorance is not bliss
Simply assuming that your organization’s current systems are secure is extremely dangerous. You need to ensure that your business and team members are as protected as possible at any moment.
We can help you develop an effective cybersecurity strategy and security program that will provide you with a prioritized roadmap of initiatives to maximize the safety and security of all your business activities. Our team of experts is ready to help ensure your company is prepared to protect its digital assets and establish business resilience.
We specialize in offering our clients up-to-date and cutting-edge technologies and services to help protect both their company’s and their client’s information and assets, including, but not limited to:
- Vulnerability assessment and Penetration testing (VAPT)
- Virtual Chief Information Security Officer (vCISO) services
- Tabletop Exercises
- Threat and Risk Assessments (TRAs)
- Fraud Risk Assessments
- Systems and Organization Controls (SOC) Reports
- Payment Card Industry (PCI) Advisory Services
- Public Key Infrastructure (PKI) Assurance Services
- Internal Audit Support
- Enterprise Risk Management
- IT Due Diligence
- Richter Guardian Executive Protection
You can’t afford to look the other way regarding cybersecurity. Our team of experts is ready to help ensure your company is prepared to protect its digital presence and safeguard its future.
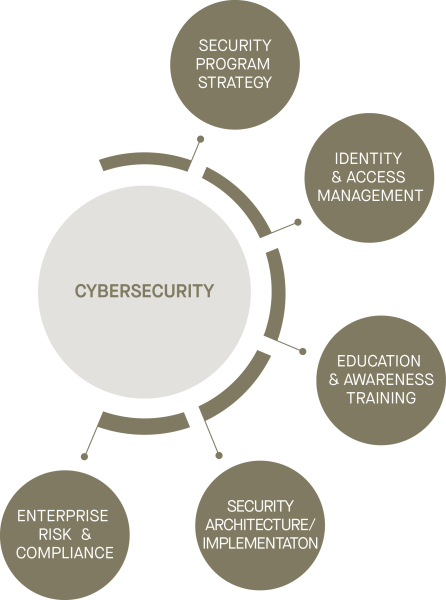
Areas of expertise in Cybersecurity
VAPT (Vulnerability Assessment/Penetration Testing)
Cyber Risk Management Support – Virtual CISO (vCISO)
Tabletop Exercises
Threat and Risk Assessments
Fraud Risk Assessment
System and Organization Controls (SOC) Report
PAYMENT CARD INDUSTRY (PCI) ADVISORY SERVICES
Public Key Infrastructure (PKI) assurance engagements
Internal Audit
Enterprise Risk Management
IT Due Diligence
Richter Guardian Executive Protection
KEY EXPERTS
View allRELATED INSIGHTS
Discover more insights
Cybersecurity: How to save, how to plan, and how to stay safe
Misconceptions and organizational deficiencies amplify the risk posed by cybersecurity threats.
Risk Management in a New Era
Cybersecurity and The Digital Privacy Act By: Mark Walsh There are two types of companies: “those that have been hacked and those …

On the flip side: do you know where your information lives?
From our Cybersecurity experts We live in a digital world. Even if it is not operating in the tech space, your …